EC2 METADATA
Information about your instance that can be customized or managed in a running instance is known as instance metadata. Instance metadata categories include hostname, events, and security groups. Additionally, you can access the user data you specified when launching your instance using instance metadata. You may include a short script or specify parameters while configuring your instance. Using user data, you can create generic AMIs and alter the launch-time configuration files. You can set up new or existing instances to carry out the following tasks using instance metadata options:
Require instance metadata requests to be sent via IMDSv2
Put the PUT response hop limit in.
Lockdown instance metadata access
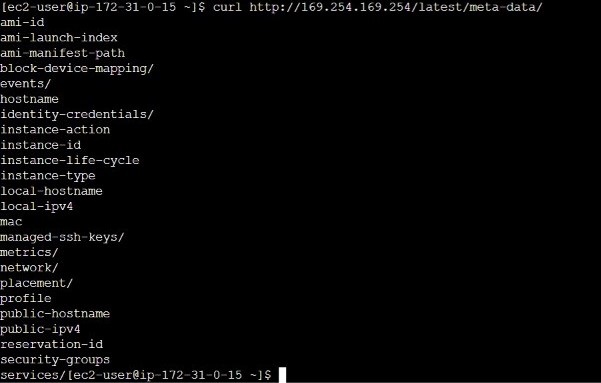
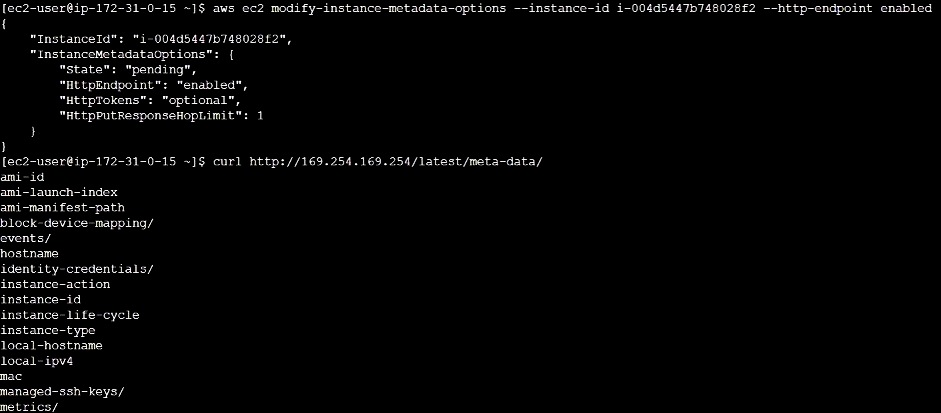
It is possible to access metadata from an active EC2 instance using one of the following techniques: IMDSv1\sIMDSv2 The Instance Metadata Service is known as IMDS. As you might assume, the methodologies are slightly different; IMDSv1 employs a request/response method, whereas IMDSv2 is session-oriented. AWS urges you to use IMDSv2, which is the preferred method. By default, the AWS SDK uses IMDSv2 calls, and you can require users to configure a new EC2 with IMDSv2 enabled by using IAM condition keys in an IAM policy. Use the following IPv4 or IPv6 URIs to view all types of instance metadata from a running instance. IPv4 curl http://169.254.169.254/latest/meta-data/ IPv6 curl http://[fd00:ec2::254]/latest/meta-data/ The IP addresses are link-local addresses and are valid only from the instance. To view instance metadata, you can only use the link-local address of 169.254.169.254 . Requests to the metadata via the URI are free, so there are no additional charges from AWS.
Need of Disabling Metadata
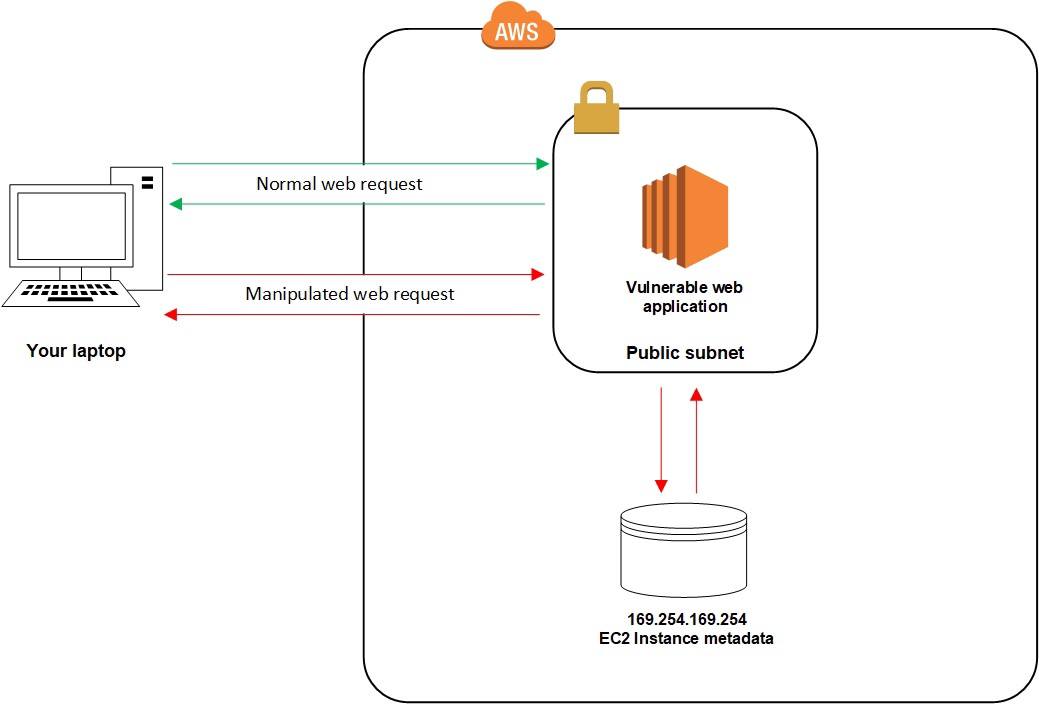
In AWS setups, the SSRF attack is frequent and well-known to everyone. Attackers that automate vulnerability scanning and gather IAM credentials from publicly accessible online applications have been found by Mandiant(A cyber security firm). Implementing IMDSv2 for all EC2 instances, which has additional security advantages, would reduce these risks for your company. The possibility of an enemy stealing IAM credentials via SSRF would significantly decrease with IMDSv2. Using Server Side Request Forgery (SSRF) to gain access to the EC2 metadata service is one of the techniques for AWS exploitation that is most frequently taught. The metadata service is accessible to the majority of EC2 Instances at 169.254.169.254. This contains beneficial information about the instance, such as its IP address, security group name, etc. If an IAM role is attached to an EC2 instance, the metadata service will also contain IAM credentials to authenticate as this role. We can steal those credentials depending on the version of IMDS in use and the capabilities of the SSRF. It is also worth considering that an adversary with shell access to the EC2 instance could obtain these credentials. In this example, a web server runs on the EC2 instance’s port 80. This web server has a simple SSRF vulnerability, which allows us to send GET requests to any address. This can be used to send a request to http://169.254.169.254.
To Disable Metadata
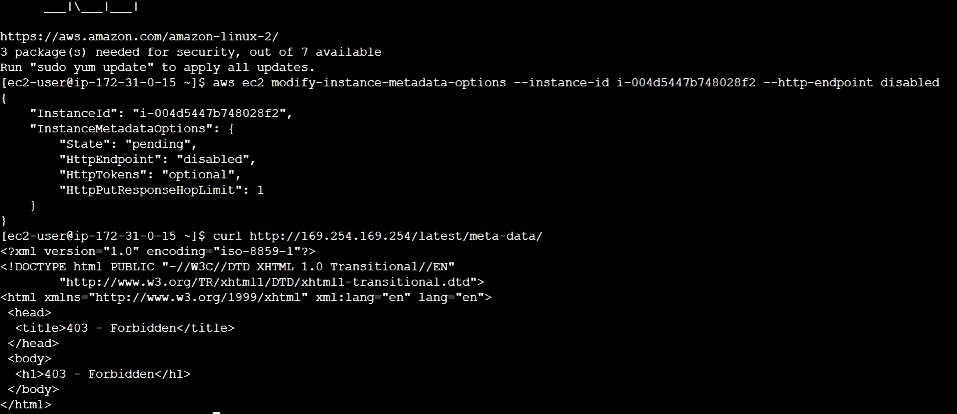
By blocking the HTTP endpoint of the instance metadata service, you can prevent access to your instance metadata, regardless of which version of the instance metadata service you are using. You can reverse this change at any time by enabling the HTTP endpoint. Use the modify-instance-metadata-options CLI command and set the http-endpoint parameter to disabled to disable metadata for your instance. To disable metadata run this command: aws ec2 modify-instance-metadata-options –instance-id i-0558ea153450674 –http-endpoint disabled You can see that after I disable my metadata, if I try to access it I get a FORBIDDEN message. If you want to enable your metadata again run this command: aws ec2 modify-instance-metadata-options –instance-id i-0558ea153450674 –http-endpoint enabled
Conclusion
Metadata can be useful for extracting information from large data stores. However, it can also be misused to know about a person’s location or identity without their knowledge or consent. Because it records every change you make, including deletions and comments, you need to be aware that it may contain information you wouldn’t want others to be able to see. As a result, removing metadata is critical to maintaining your online privacy and anonymity. You may also explore some AWS Key Terminologies that advance your AWS Learning.